Okay, so I messed around with this thing called “fauxre leaks” today, and let me tell you, it was a bit of a trip. I’m not gonna lie, I kinda stumbled into it, but hey, that’s how we learn, right?

First, I had to, you know, actually get the tool. Thankfully you don’t need to perform any compilation, it can be used right away.
Then, I wanted to really see what this thing could do. So, I run the tool, and the first attempt show that the tool need root privileges, so, I run again with sudo, so I get the full report.
Once I had the PID, it was time to dig in. That’s where fauxre leaks came in. I fired it up, pointed it at the process, and… boom. A whole bunch of stuff started scrolling by. Honestly, a lot of it was just gobbledygook to me at first – memory addresses, hex values, the works.
But then, I started to see some interesting bits. Strings, mostly. Stuff that looked like it might be configuration settings, maybe even some data that the program was working with. It wasn’t super clear, but it was definitely something.
I am not expert with memory, but the results are easy to understand.
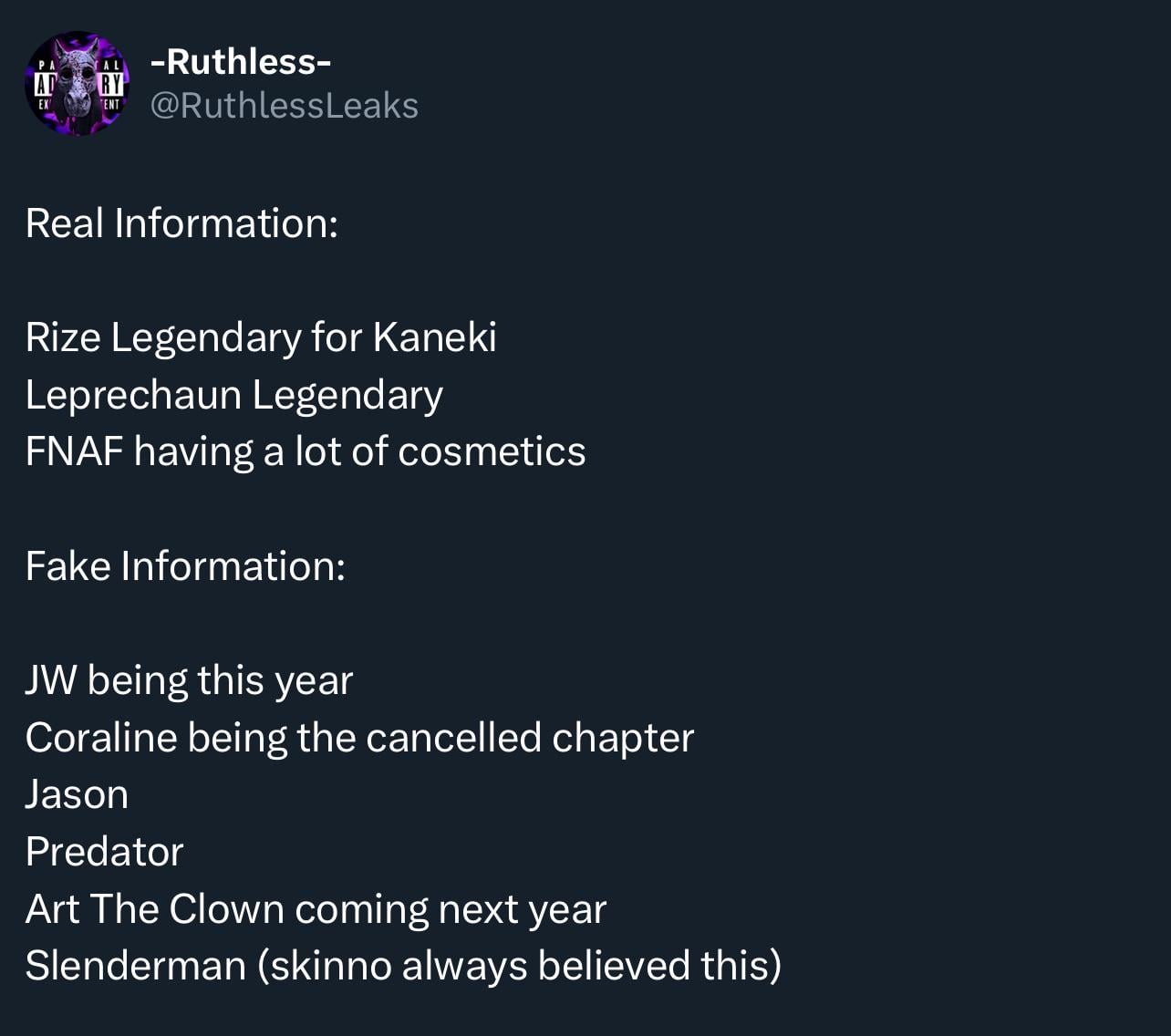
So, yeah, that was my day with fauxre leaks. It’s a powerful tool, for sure, but it definitely takes some practice to get the hang of it. I’m still figuring it all out, but it’s pretty cool to see what’s going on “under the hood” of a running program. It’s like peeking behind the curtain, you know?